The post Securing Kuburnetes with StackRox appeared first on ITEnterpriser.
]]>The Outlook is Cloudy
There’s no stopping the inexorable rise of cloud computing. From the early days when it simply providing remote storage, it has brought innovation after innovation. Software-as-Service, Platform-as-a-Service, Infrastructure-as-Service, you-name-it-as-a-service. The uptake has been swift and widespread, and the impact on the traditional view of IT infrastructure has been profound.
In particular, the ability to quickly spin up preconfigured and computationally-cheap servers that are used for short tasks and then discarded has disrupted conventional thinking about the need for on-premise server hardware. On-premise hardware servers were replaced by fully-loaded cloud-hosted virtual servers. But the whole premise of remotely hosting a fully-loaded virtual machine that simply replicated the on-premise hardware it replaced is under question.
Platform-as-a-Service providers deliver OS-level virtualization. This permits containers that incorporate the software, dependencies, and configuration files required for them to be created and spun-up, auto-configured, and populated with the appropriate packages. The DevOps world talks of “cattle not pets” as a way to distinguish between the short-term commodity model of servers as containers, versus the high-maintenance, long-term investment in traditional fully-loaded servers.
Because a container-based infrastructure can scale rapidly and shrink again as demand requires, and because containers can communicate through well-defined channels, the IT estate of many organizations has become incredibly dynamic.
In particular, DevOps has embraced the cloud and containers and thrived because of it. Since DevOps was first promoted at DevOpsDay in Belgium in 2009, it has brought about a revolution in the philosophy and practices behind software development and systems administration and operations. The speed, quality, and collaborative benefits of DevOps are achieved by automating as many processes as possible. Automating code testing, workflows, and deployment is dependent on automated infrastructure. And that means containers. Lots of them.
With so many containers sitting on the critical path between coding and runtime it cries out for a management tool to monitor, control, and administer those containers. Kubernetes is just such a system. It is a container orchestration system that automates the deployment, management, scaling, and networking of containers.
That all sounds great. Now how do we make it secure?
Security for Containers and Kubernetes
As the popularity and adoption of containerization continue to grow, the need for a dedicated security system becomes more evident. Containerization makes the cloud look like a swarm of interconnected, yet independent, mini-clouds that are being created and retired on-demand, automatically.
Retro-fitting conventional security measures onto that type of environment will not give you complete cover, nor visibility into what’s happening inside your dynamic fleet of containers. Plainly, this requires a security tool designed to satisfy the unique requirements of this type of infrastructure.
StackRox is an example of this type of defensive system. Cleverly, it leverages the capabilities and core purposes of Kubernetes instead of trying to interface with the containerized environment itself. That makes StackRox agnostic as far as container technology is concerned. Kubernetes groups containers into logical units to simplify their administration, monitoring, and management. There’s no point in re-inventing the wheel, so StackRox leaves all that to Kubernetes. StackRox talks to Kubernetes, and Kubernetes talks to the containers.
StackRox lets you monitor your Kubernetes installation for attacks or threats and visually review the state of your container estate. It installs itself as a collection of lightweight services. These interwork with Kubernetes to access all the information that Kubernetes retrieves regarding the containers. Because Kubernetes has a detailed understanding of the containers during each of the building, deployment, and in-service phases, StackRox does too.
The StackRox Model
StackRox uses collections of rules and requirements called policies. It comes with a set of 66 best practice security policies. Each of these policies is a set of rules defining security or compliance requirements or restrictions. You can create your own policies to suit any special cases you may have.
StackRox is smart. For example, it can suggest the policies that you should enable according to the activities you’re involved in, or the type of containers you are configuring. Because StackRox is integrated right into Kubernetes, the Kubernetes scripts and the StackRox configurations can all be treated as code, and version controlled. It means all of your staff work from a single source of truth.
StackRox scans your Kubernetes estate for vulnerabilities with instant alerting to the nominated team members, as well as image scanning of the containers themselves. This happens from a container’s build phase through to its runtime. Non-compliant images found in the build phase are rejected, and the DevOps team is alerted through their continuous integration system or another preferred route.
In the deployment phase, security mechanisms can adjust permissions so that containers with vulnerabilities do not reach the runtime phase. Perhaps a container does not need internet access but that permission has been granted in error. That container should be restricted and a message send to the DevOps team so that they can adjust the container.
StackRox prioritizes the vulnerabilities it finds according to the level of risk and the severity of the vulnerability. This allows the corrective and remedial work to be prioritized. StackRox allows you to automate much of the remediation.
StackRox also takes into account the organization’s appetite for risk, as detailed in the security policies. Even when the container deployments are running, the scanning continues.
A Tough Nut Cracked
Security monitoring, scanning, and alerting systems often fail in cloud environments—especially fast-paced and dynamic environments that DevOps require. StackRox provides a preemptive strike by scanning the build and deployment phases of your containers, as well as the running instances. With suitable automation, it can address most vulnerabilities before the containers are deployed.
StackRox enhances the reporting in Kubernetes to provide visibility to vulnerabilities across all your running containers. StackRox delivers timely alerts and automatic incident response. It provides similar functionality for compliance requirements, with automated and on-demand validation checks to ensure regulatory directives are met and data is protected, with out-of-the-box support for CIS, NIST, PCI, HIPAA, and more.
A collection of dynamic container clusters is a serious challenge to make secure. StackRox does all the heavy lifting for you by scanning container images from creation to deployment and detecting runtime attacks using its policies of rules and restrictions, behavioral analysis, and vulnerability database.
StackRox has features that facilitate everything from auditing access to customer environments to giving you what you need to easily complete vendor security assessments. If you’re wrestling with the security concerns and compliance difficulties coming from your container estate, put StackRox on your shortlist of tools to consider.
The post Securing Kuburnetes with StackRox appeared first on ITEnterpriser.
]]>The post ExpressVPN Review: How Does It Perform (and How to Install) on Ubuntu? appeared first on ITEnterpriser.
]]>What is VPN?
A Virtual Private Network is a fundamental part of staying safe and anonymous on the modern web. By encrypting your internet traffic and sending it through its own network of servers, a VPN prevents anyone from eavesdropping on your internet traffic and it prevents anyone tracking your traffic back to your genuine IP address. That gives you security and privacy.
It also circumvents geographic limitations. If a website or other internet service is not available to internet users from your country you can use a VPN to make it look like you’re actually located in a country where that service is permitted. As long as your VPN provider has servers in that other country, of course.
ExpressVPN has more than 3000 servers located in 160 data centers in 94 countries around the globe. It has desktop clients for Windows, Mac, and Linux. There are ExpressVPN apps for both iOS and Android. They also provide browser extensions for Chrome, Firefox, and Microsoft Edge. On paper, ExpressVPN has an impressive global infrastructure and a global spread of servers, an impressive stable of cross-platform clients, and extensions for the major browsers. But how easy is it to install and use?
We’re going to walk through what is probably the most complicated of all of the desktop installations. We’re going to install ExpressVPN on Ubuntu Linux, install the extension on the Linux version of Firefox, and see how they perform.
Installing ExpressVPN on Ubuntu
We’re using the most recent version of Ubuntu, the 21.04 Hirsute Hippo released in April 2021. We also tested the entire process on Ubuntu 20.10, the October 2020 release code-named Groovy Gorilla.
ExpressVPN is available in the usual Ubuntu program repositories, but it’s best to install the latest version from the download page on the ExpressVPN website. Use the drop-down menu to select the Ubuntu 64-bit version. The versions available are:
- Ubuntu 32-bit and 64-bit
- Fedora 32-bit and 64-bit
- Arch 64-bit
- Raspbian 32-bit
It’s good to see other Linux distributions get some attention, including Raspbian—now called Raspberry Pi OS—for the Raspberry Pi single-board computer. But we need the Ubuntu 64-bit version, so select that in the menu and then click the green “Download” button.
The “.deb” package file will be downloaded to your computer. You’ll probably find it in your Downloads directory.
You could install it by double-clicking it in your file browser. This will launch the Ubuntu software application and install it for you. Perhaps you’re installing ExpressVPN on a server with no GUI installed on it, or over an SSH connection, or you just prefer to do things the command-line way. The command you need is:
sudo dpkg -i expressvpn_3.7.0.29-1_amd64.deb
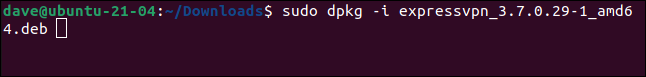
Make sure you spell the name of the file you’ve downloaded correctly. Our version of ExpressVPN was 3.7.0.29. That part of the file name will change with later versions. Helpfully, if you type the first few letters of the file name and press the “Tab” key, the rest of the file name will be completed for you.
You must activate ExpressVPN before you can use it. Activation requires an activation code. You’ll receive an activation code when you purchase a plan. At the time of writing the costs in U.S. dollars are:
- $12.95 per month, for 1 month
- $9.99 per month, for 6 months
- $8.32 per month, for 12 months
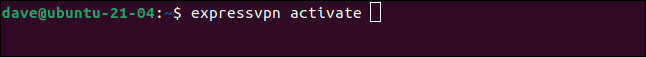
To activate your installation of ExpressVPN type:
expressvpn activate
When you’re prompted for the activation key enter the key that has been emailed to you. Note that it isn’t displayed on-screen when you type it. Because of the gobbledegook nature of the key and the difficulty you’ll have typing it sight unseen, it’s much safer to copy and paste the activation key into the terminal window. You still won’t see the key displayed in the window, but there’s no chance of mistyping it. Note that the key combination to paste into the terminal window is “Ctrl+Shift+V” not “Ctrl+V.” When you’ve pasted the activation key hit “Enter.”
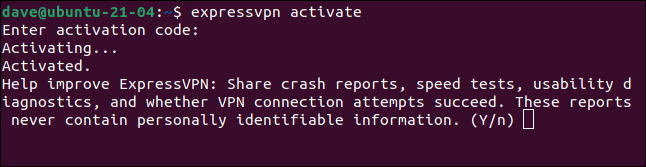
If all goes well you’ll see the “Activation” confirmation. You’ll be asked whether you want to send usage reports to ExpressVPN. Press “Enter” to agree, or press “n” to opt out. You’re now ready to start using ExpressVPN.
Using ExpressVPN
The simplest way to make a VPN connection is to let ExpressVPN choose which server to connect to.
expressvpn connect
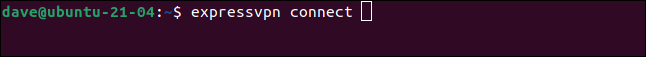
ExpressVPn establishes the connection, displays the name of the connection, and provides some help text.
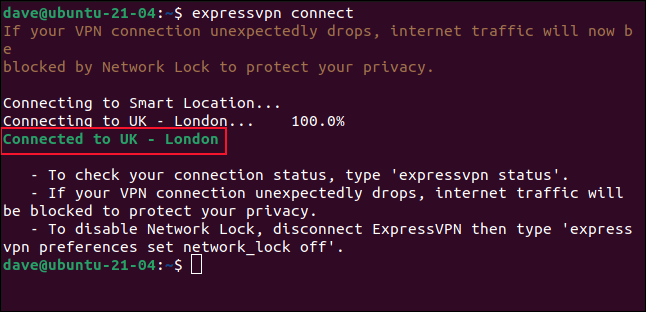
In this example, it has connected the computer to an ExpessVPN server located in London. At any time you can check the status of the connection by typing:
expressvpn status
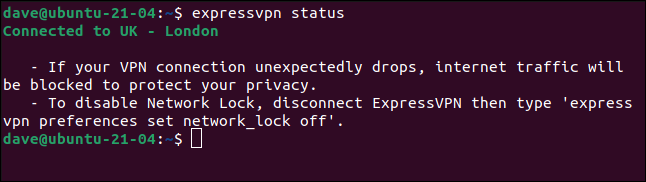
When you no longer need the VPN connection, type:
expressvpn disconnect
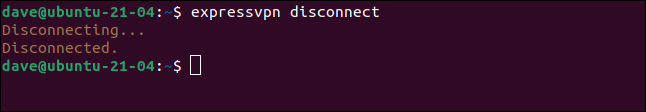
The VPN connection is closed and you’re returned to your normal internet access.
Connecting to a Server in a Specified Country
If you need to make your connection appear as though it originated in a specific country, pass the country on the command line. If we wish to appear as though we’re in Germany, we’d use this command:
expressvpn connect germany
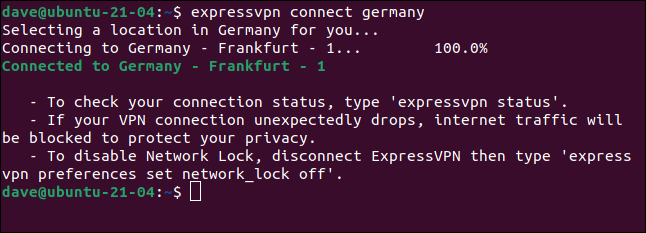
The VPN connection is established using a server in Germany. To see a list of the countries in which ExpressVPN has servers, use this command. We’re piping the output into less because there’s quite a lot of it.
expressvpn list all | less
There are four columns of data in the output.
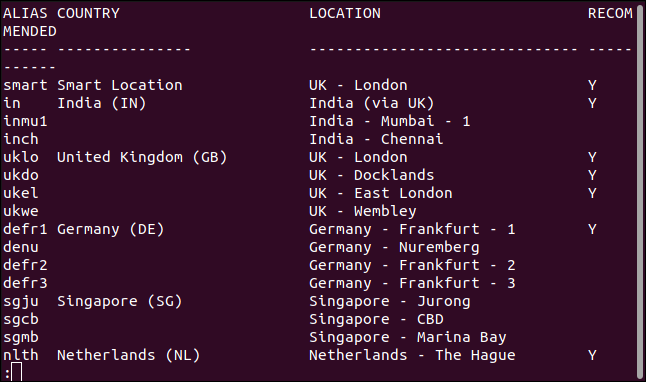
- Alias: This is the name you use if you want ExpressVPN to connect to that server.
- Country: The country in which the server is located.
- Location: The city in which the server is located.
- Recommended: Whether the server is recommended for general use. If it isn’t, you can still use it but your speed might not be as fast as it is on other servers. They’ll do in a pinch if you really need to appear as though you’re in that specific country. Generally, you’ll pick a recommended server.
Installing the Browser Extension
We’re going to install the browser extension in Mozilla Firefox because that’s the default browser in Ubuntu. The process is similar for all browsers. You can install the ExpressVPN extension through Firefox’s extensions web page, but that didn’t work for us. The only reliable method we found was to install the extension through the command line. Make sure you have ExpressVPN installed and working before you install the extension.
The command to use is:
expressvpn install-firefox-extension
This launches Firefox if it isn’t already open. It takes you to the extension installation page on the ExpressVPN website. Click the green “Get Extension” button.
The browser extension is downloaded to your computer. The page changes to allow you to install the extension. Click the blue “Add to Firefox” button.
A permission dialog appears.
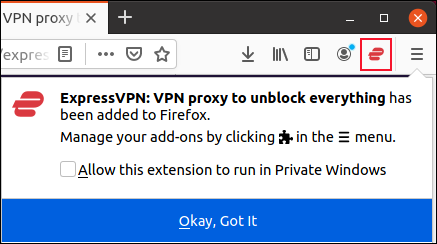
Click the blue “Add” button. When the extension is installed you’ll see the ExpressVPN icon in the top-right corner of your browser window. A reminder dialog tells you that you can manage your extensions through the Firefox three-line “hamburger” menu. It also allows you to check a box if you want to use the ExpressVPN extension in Private Windows. When you’re ready to proceed, click the blue “Okay, Got It” button.
Using the Browser Extension
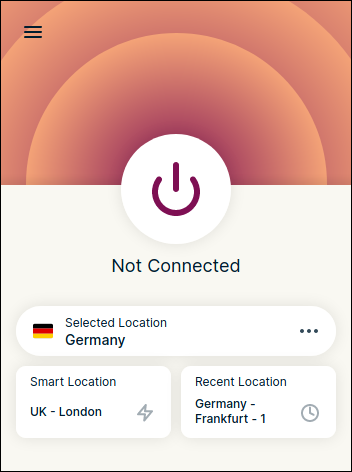
To use the extension, click the ExpressVPN icon in the top-right of your browser window. The extension window opens. It’ll tell you you’re not connected. The entire top half of the window is the button you use to connect and disconnect. The bottom half shows some recent connection details. What you’ll see will depend on which connections you’ve recently made. On our research machine, three locations are listed.
- Selected Location: This is the connection you’ll make if you click the connect button.
- Smart Location: This is a location chosen for speed and geographical proximity. A close fast server will give you the best performance.
- Recent Location: This is the most recent location you connected to, that wasn’t a “Smart Location.”
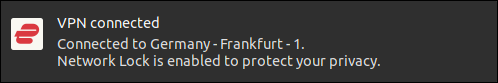
Clicking the button in the top half of the window connects you to the “Selected Location.” Clicking the “Recent Location” button connects you to that location. A notification appears at the top of your screen.
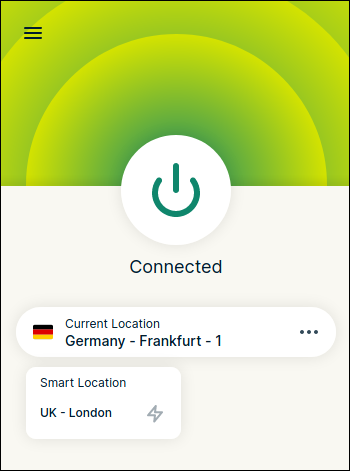
And the top half of the extension window turns green to show you’re connected.
A small green tick appears on the ExpressVPN icon in the top-right corner of your browser window to indicate you’re connected.
If you click the button in the extension window once more the connection is disconnected, the top half of the window returns to the reddish-orange color. You can give feedback to ExpressVPN about the quality of the connection by clicking a green thumbs up or a red thumbs down.
If you click the “Smart Location” button you’re shown a list of possible locations. Clicking one of them will connect you to that location.
How It Performed
In our tests, ExpressVPN was nothing but reliable. It connected quickly every time—within two or three seconds—and every connection was fast. We had no drop-outs or slow-downs. Of course, our tests only took place over a couple of days. If you use the service for a longer period perhaps you’ll see the occasional blip, but for us, it was plain sailing.
ExpressVPN understandably takes security seriously. ExpressVPN uses AES-256 encryption, a 4096-bit SHA-512 RSA certificate, and Hash Message Authentication Code (HMAC) to prevent modification of data in transit. They even have their own encrypted, no-logging, private Domain Name Servers on every one of their own servers.
The problem with some other VPNs is their policy and practices on logging. Some of them log so much information it pretty much negates the whole point of using a VPN. ExpressVPN is clear about what is and what isn’t logged. Nothing is logged that can identify your IP address or your browsing history.
They do log some performance information such as the dates when connections were made, which servers were connected to, and how much data has been handled by their VPN connections each day. None of this can be used to identify any of their users. And all of this has been confirmed by an independent audit conducted by PricewaterhouseCoopers.
In case you need it, the command to install the browser extension in Chrome is:
expressvpn install-chrome-extension
You can read the manual page for ExpressVPN using this command:
man expressvpn
In Summary
This is a first-class VPN. Whether you hang around the command-line or prefer to use the browser extension, you’ll find that ExpressVPN is easy to install and easy to use. Easy to install, that is if you remember to use the command line to install the browser extension. Once we’d figured that out it repeatedly installed the browser extension time and again both in Firefox and Chrome with no issues.
The sensible defaults and smart location connection capability make using ExpressVPN an absolute breeze. It’s just a little dearer than most of its direct competitors, but you get what you pay for: rock-solid performance, fast throughput, and an almost overwhelming choice of countries and locations.
You can install ExpressVPN on any number of devices with any mix of operating systems. Any five of those devices can be connected at once. The verified no-logging policy is worth the price of admission by itself.
The post ExpressVPN Review: How Does It Perform (and How to Install) on Ubuntu? appeared first on ITEnterpriser.
]]>The post What is Whistleblowing, and How to Remain Anonymous appeared first on ITEnterpriser.
]]>Types of Whistleblowing
Whistleblowing is the common name for what is more formally called making a disclosure. It can mean bringing some wrongdoing to the attention of management within an organization, or to external authorities, or to the attention of the public via the media. in extreme cases, it can involve disclosing to the outside world of wrongdoings by a government or other ruling faction in an oppressive regime.
Not everything you may disclose will count as whistleblowing. Reporting these types of event are considered whistleblowing:
- A criminal offence, for example someone is defrauding your organization. The organization is the victim.
- An organization is breaking the law. The organization is the wrongdoer.
- Something that jeopardizes the health or safety of a person.
- Something that either puts the environment at risk or actually damages it.
- A miscarriage of justice.
- Someone is covering up a wrongdoing.
- Violations of human rights.
However, anything to do with bullying, harassment, or discrimination at work is not considered whistleblowing in most jurisdictions. The difference is important.
Whistleblowers are protected by law in many countries. In the U.S. the Whistleblower Protection Act of 1989 protects federal whistleblowers. In the United Kingdom, the Public Interest Disclosure Act 1998 provides similar protection and the “right not to suffer detriment” for whistleblowing. In Europe, the EU Whistleblower Directive protects people who report breaches of European Union law.
There are many other pieces of legislation and statutes that uphold the rights and protection of whistleblowers. The U.S. Department of Labor’s Occupational Safety and Health Administration has a Whistleblower Protection Program. It protects workers from detriment should they report a breach in any of more than 20 federal laws.
Who Do You Disclose to?
What you’re disclosing will usually dictate who you disclose it to. If it is something about a colleague you’ll probably be reporting it to a member of the management team of your organization. Many organizations have a whistleblowing process. This should outline the steps they have in place to safeguard your anonymity.
If you’re unhappy about revealing your identity because of fear of reprisals, you can report the wrongdoing anonymously. There can be an awkward balance at play here. Your organization may or may not be able to proceed with the complaint if you withhold your name, but providing your name gives rise to a risk of exposure. If you’re whistleblowing on your manager it would create an untenable situation if they later discovered who the whistleblower was.
There might be a prescribed person or body that you can disclose to anonymously. If you’re reporting an organization and not an individual, it will usually be to a prescribed body, professional body, or a trade association.
If you’re wanting to draw world attention to a breach of human rights you’ll need to approach an organization like the United Nations.
You can also whistleblow to the media to bring wrongdoings to the attention of the public and the relevant authorities. Most major media organizations have guidelines regarding anonymous sources. Online resources like WikiLeaks are also popular with whistleblowers.
The media organization will probably require your name in order to pursue the story, but you’ll be protected as an anonymous source. This is a right accorded to journalists by law in many countries and under international law. It prohibits attempts to compel them to reveal their anonymous source. This is doubly important because whistleblowing to the media waives your rights in law to protection as a whistleblower. Without anonymity—or if your anonymity is broken—you will face the possibility of reprisals.
- You might get demoted, repositioned, transferred, or lose your job altogether if you are still working at the organization in question when your identity is revealed.
- You might be seen as untrustworthy and a traitor. You might become the victim of workplace bullying.
- Other businesses in the same industry could add you to a blacklist, making future employment difficult if you choose to leave your current organization.
- You might face legal action if you break any laws to gather evidence to justify or support your whistleblowing claims. Even with the legal protection for whistleblowers, there is no protection for breaking the law.
- If you’re whistleblowing on an oppressive regime your life may be at risk.
Preserving Your Anonymity
Communicating and delivering documents anonymously isn’t as easy as you might think. Almost everything we do to communicate or transmit data leaves a trail of breadcrumbs that can lead right back to you or has a log that records what you did and when. It isn’t easy to act anonymously, but it isn’t impossible either. Knowing what type of tracking and logging exists allows you to avoid many common mistakes.
The run-of-the-mill email account isn’t anonymous. It is tied to your identity so that you can receive your email. And you have to provide information about yourself—and verify it—before you can set up most email accounts. And anyone who can access the email system logs—either through administrative capabilities or via a subpoena—can see who you have been communicating with.
However, there are free, secure, privacy-focused, and anonymous email services that you can use. ProtonMail is one of the better known. Your email is encrypted. Even ProtonMail cannot access your emails. It’s a web-based service so you don’t need to have an application installed anywhere to send or read your email.
Crucially, you can sign up for the ProtonMail service without providing any information about yourself. They do ask for some means to contact you in case you lock yourself out of your account and they need to verify it is you before they restore access to you. However, that is optional. If you don’t want to, you don’t need to provide any information about yourself at all. Just make sure you don’t forget your password.
You’ve now got an email address that is secure, encrypted, and not linked to your identity in any way. But now you have to be able to use it so that your online activity doesn’t point back to you.
Exfiltrating Data: Gathering the Evidence
There’s a great saying “computers serve their owners, not their users” and it’s good to keep that in mind. If you’re using someone else’s computer you don’t know what is being logged. It could be anything from the usual internet browser activity and system logs to a full corporate employee monitoring system. These systems can:
- Capture keystrokes.
- Detect file copy actions.
- Detect document creation, edits, and deletions.
- Detect and log, or prevent, the use of a USB memory drive.
- Take a screenshot every few seconds.
But even in the absence of employee monitoring software, you can’t trust a corporate computer, an internet cafe computer, or the computers in your library. You can’t purge and clean them to remove all traces of your activity. Router and firewall logs also track what you do. And you might well be on CCTV too.
Obviously, don’t use your work computer for whistleblowing activities, and don’t check your ProtonMail from your work desk. But the problem is, if you need to exfiltrate files that contain evidence of the wrongdoing how can you achieve that?
If you have a hard copy of the files and it is feasible, you can photocopy them. If that’s out of the question—some corporate photocopiers require an ID to identify the employee before they can be used—covertly remove the hard copies that you have. You can then scan them or photograph them at home and return the originals when you’ve finished. Don’t take them to a photocopy shop.
Trying to covertly print at work is dangerous. Large corporate printers log who has printed what and when. Some of them even keep copies of the documents that pass through them. And printing at home isn’t anonymous either if you have a color laser printer.
Many domestic color printers fingerprint pages with tiny yellow on white dots that identify the time, date, and serial number of the printer the printouts came from. If you’re considering sending a letter or a covering note with the exfiltrated documents, don’t use a color printer.
If hard copies are not a possibility and you have to gather electronic documents, you have some options. The hard part is knowing which of the possible actions is going to be detected and reported as a suspicious activity—if any. Some organizations are lax when it comes to data protection automation.
You may be able to upload files to private cloud storage such as OneDrive, Google Drive, DropBox Evernote, or an anonymous, free, file-sharing site like GoFile.
If you have administrative access to a private website you can try using a File Transfer Protocol (FTP) browser plug-in and FTP the files to the storage in the website.
Plugging a smartphone into a computer’s USB port to charge it is common practice. But smartphones can also store files, allowing data to be copied to them as though they were a USB memory drive. If USB drive access hasn’t been turned off, this might be less eye-catching than using a regular USB drive.
Emailing files is too traceable to be anything other than a dire, last-ditch option.
If you’re not going to be caught on CCTV camera, taking photographs of your screen or of the hardcopy documents is a long-winded possibility.
Dealing With Metadata
Electronic documents, especially those created with office productivity suites such as Microsoft Office contain metadata. Metadata is data that describes the document itself. It is automatically created by software applications. Metadata holds information such as:
- The name and version of the package that created the document.
- The name (or network ID) of the original author.
- The date and time when the document was created.
- The name (or network ID) of the person who last edited the documents.
- The date and time when it was last edited.
Some of that data could incriminate you.
Photographs taken with a digital camera or a smartphone contain a wealth of information about the image including when it was taken, the details of the device used to take the photograph, and the GPS coordinates of where the image was taken. If you’ve taken hardcopy documents home and photographed them the GPS location of your home is likely to encoded within the images. That will directly implicate you as the whistleblower.
Here are the number of pieces of data found in a few sample files from one of my computers. Your documents may contain even more metadata than these, depending on your device and software settings.
- 45 Metadata Fields: Microsft Word “.docx” word processing file.
- 34 Metadata Fields: Microsft Excel “.xlsx” spreadsheet file.
- 102 Metadata Fields: JPG image taken on a smartphone.
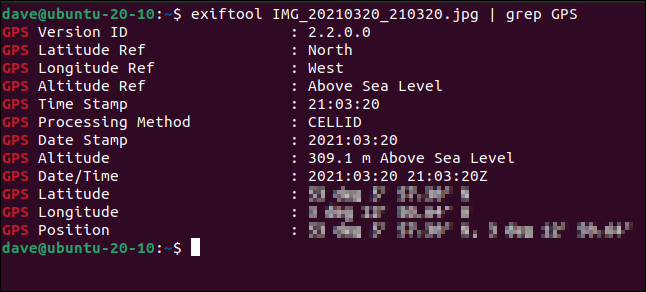
Clearly, if you are going to deliver electronic documents and images to your contact and you wish to remain anonymous you need to erase or edit the metadata. Free tools exist for this and are available for all common computing platforms. ExifTool is one of the most capable. It is free, cross-platform, and capable of working with the metadata of over 190 different file types.
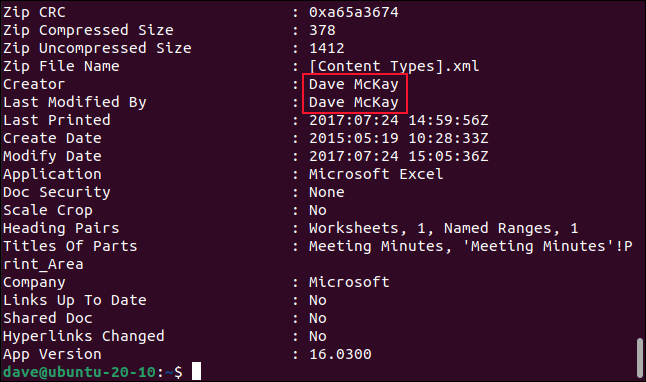
ExifTool is a command-line tool, but if you’re not comfortable with the command line you can download jExifToolGUI, which is a free, cross-platform GUI for ExifTool that works on Windows, Mac, and Linux.
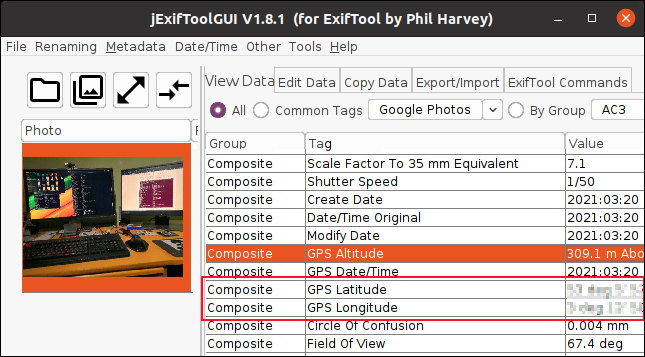
jExifToolGUI makes it easy to delete metadata fields that contain information that could be a clue to your identity.
Making the Disclosure
Assuming you have gathered the evidence, you need to make the disclosure. That means making contact with the party you are disclosing to. Most major newspapers and many other organizations have a means of obtaining anonymous news stories and tip-offs, using SecureDrop to provide a portal for file transfer. Because SecureDrop portals are hosted on the Dark Web you’ll need to use a Tor-enabled browser such as the Tor browser to access them.
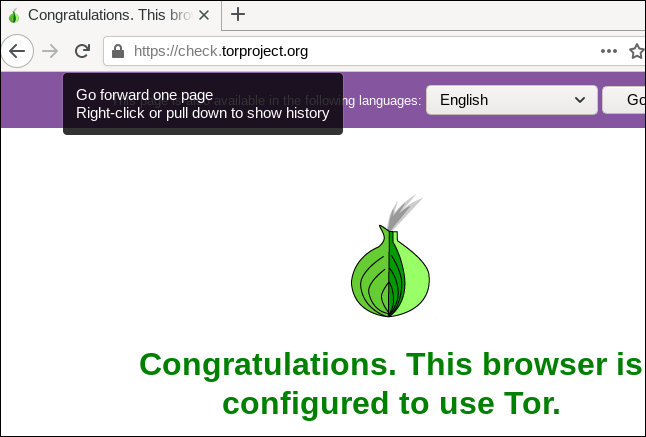
For example, the New York Times SecureDrop portal is located at: https://nytimes.securedrop.tor.onion, and can only be accessed using a Tor-enabled browser.
The Tor anonymous network makes it virtually impossible to backtrack and find out your IP address, so you cannot be identified. If you need to communicate with an organization that doesn’t use SecureDrop you should check their website for details of how to contact them for confidential matters. Use a Virtual Private Network at the least, and a Tor-enabled browser by preference, when contacting any site for any aspect of your whistleblowing. That includes the relatively benign act of finding out what the address of their SecureDrop portal is, or looking up other contact details.
Once you’ve made contact, leave your ProtonMail or other secure email address so that they can get back to you. Once you’ve communicated back and forth for a period of time and you’re comfortable with your contact, you may choose to connect with them using Signal Messenger, a secure, private messaging service.
Signal is private, but it isn’t anonymous. If the authorities want to, they can subpoena Open Whisper Systems—the creators of Signal—and find out whether you use the service, when you joined, and when you last used it. But that’s all they can discover because that’s all that the Signal services stores about you. No one can determine with whom you have communicated, or about what. If you want to have voice calls with your contact do it from your home, and use Signal’s voice call capability.
If you want to have the strongest possible protection for your online anonymity, use Tails. Tails is an operating system that sits on a USB memory stick or CD. You boot your computer using the image on the memory stick or CD, and it runs a privacy-focused minimalist Linux based on Debian. It already has the Tor browser installed for you.
You can check your secure mail, access secure portals, and do whatever you need to. When you shut down, remove the memory stick or CD and you can boot your computer back up as normal, into its usual operating system. Nothing on your computer will have any traces of what you’ve done. And Tails is an amnesiac operating system. It doesn’t track anything you do.
If you want to go a step further use public Wi-Fi, and Tails. But remember that many places have CCTV, including public transport, and that you should leave your smartphone at home because of its geolocational tracking. That can be used to place you at a location at a particular time which could be cross-referenced with the Wi-Fi router logs looking for encrypted or Tor connections. That could be enough to incriminate you.
If you’re going to post hardcopy files to your contact, use a post office that is outside your normal area and pay by cash. You need to avoid tying a payment card to a record of postage. Make sure there is nothing incriminating on the outside of the envelope or packaging. Every single item that is handled by the U.S. postal service is photographed. You should assume other countries have similar programs.
It’s Difficult, But Possible
Take all the defensive steps you can. Don’t just turn on incognito mode and hope for the best.
The post What is Whistleblowing, and How to Remain Anonymous appeared first on ITEnterpriser.
]]>The post How to Set Up TrueNAS CORE and Connect to it From Ubuntu appeared first on ITEnterpriser.
]]>TrueNAS CORE
TrueNAS CORE is the successor to FreeNAS. It’s a free and open source Network-Attached Storage (NAS) application. It’s produced by iXsystems Inc. and the TrueNAS community. iXSystems produce hardware and software NAS solutions for business of all size. They have hardware solutions tailored to home and small businesses, small to medium enterprises (SMEs), and enterprise-scale units for mission-critical applications.
All of their systems use the ZFS file system. The ZFS file system is remarkably robust and to a great extent self-healing. It can store zettabytes of data, supports RAID natively, and incorporates copy-on-write. The ZFS system architects and software developers—working for the legendary Sun Microsystems—went to extraordinary lengths to guarantee the integrity of the file system and to make sure ZFS wouldn’t lose data.
TrueNAS Core is the community edition of the enterprise-class software and OS used in the commercial product offerings. You can download a TrueNAS CORE ISO image, populate a spare PC with some fast, cheap hard drives, install TrueNAS on it, and have a fully-featured, modern, professional-quality NAS for your own network.
We’re going to do just that, and also show how to connect to your TrueNAS CORE from Ubuntu.
Installing TrueNAS Core
System Requirements
You need a hard drive—mechanical or Solid State Drive (SSD)—to install the TrueNAS CORE system on, and some drives to save data on. You can’t save data to the system drive. You only get redundancy with more than one data drive, so as a minimum you really need one hard drive for the TrueNAS system and two drives for data. TrueNAS advise that these drives should use conventional magnetic recording (CMR) techology and not shingled magnetic recording (SMR) technology.
You need a minimum of 8GB RAM for TrueNAS CORE. If you’re using more than eight data drives you need an additional 1GB of RAM for each additional drive over the eight.
Get the TrueNAS CORE installation Image
Download the TrueNAS Core installation ISO image. If you’re installing TrueNAS CORE on a computer with a CD-ROM, burn the ISO image to CD. If you’re installing TrueNAS from a USB memory stick, use a tool such as Etcher to create a bootable memory stick from the ISO image.
The Installation Process
Boot from the installation media. You’ll see the installation welcome menu.
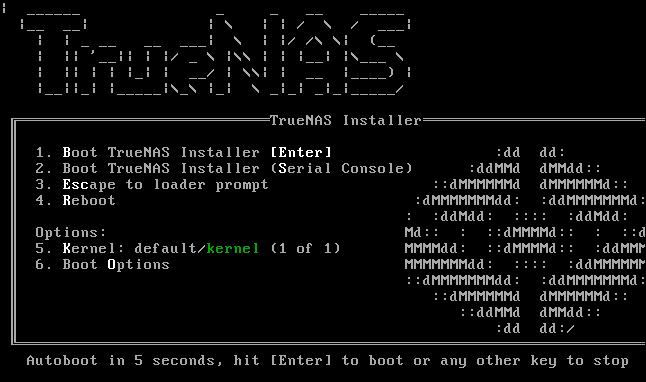
Hit “Enter” to continue. The install, reboot, or shutdown menu appears.
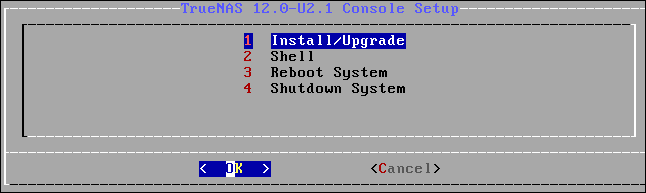
We’re going to install, so highlight option 1 and press “Enter.” The disk selection screen appears.
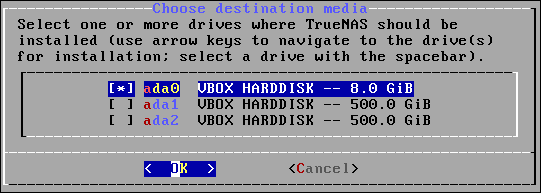
We’re installing TrueNAS CORE on the first drive. Highlight the first drive and hit “Space” to select it. Then press “Enter.” TrueNAS CORE reminds you that the drive will be wiped, and gives you chance to back out.
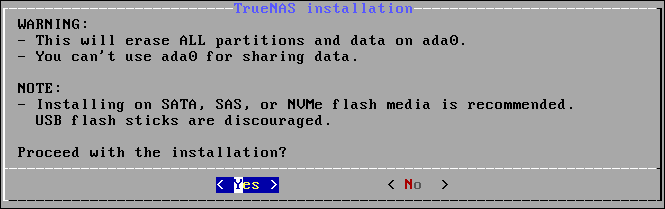
Highlight the “Yes” option and press “Enter.” The root password screen appears.
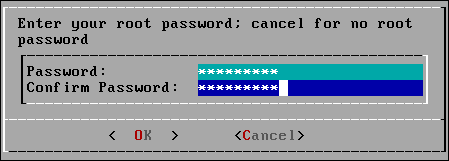
Type in a password for the TrueNAS CORE root user. Make sure you remember the password. You’re going to need it to log into TrueNAS CORE. You must type it twice.
Highlight the “OK” button and press “Enter.” The boot type menu will appear. You can choose to boot your TrueNAS CORE in UEFI or BIOS modes.
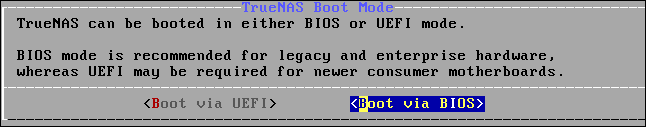
Select either “Boot with UEFI” or “Boot with BIOS” according to the vintage of your TrueNAS CORE computer, then press “Enter.” The installation process will start. It completes surprisingly quickly. When it has completed you’ll see the installation completed notification screen.
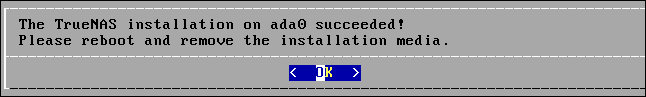
Press “Enter.” The install, reboot, or shutdown menu appears.
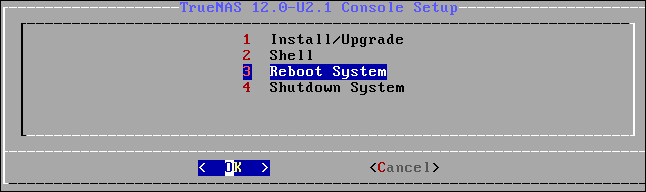
Highlight option 3, press “Enter”, and eject the installation media. The computer will reboot and start TrueNAS CORE. The first time TrueNAS CORE boots it takes longer than usual because one-time configuration steps are performed. Very shortly you’ll see the TrueNAS CORE boot menu.
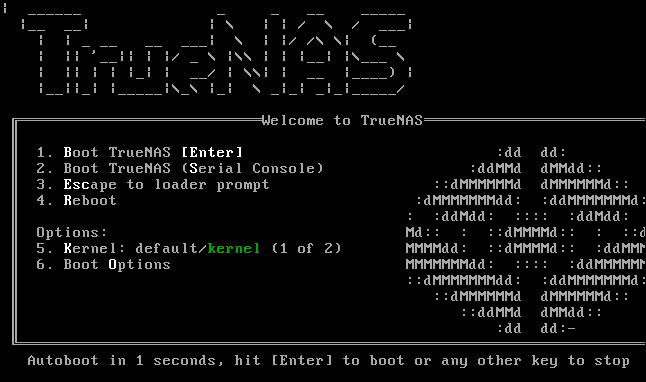
Press “Enter” or wait five seconds to boot into TrueNAS CORE. Presently you’ll see the TrueNAS CORE console application.
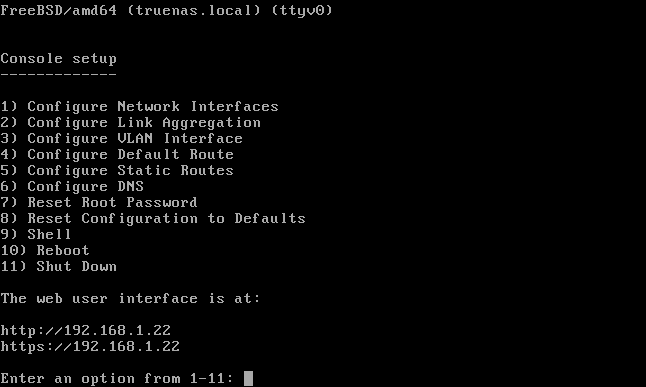
The only thing you need to take note of here is the IP address of the web interface.
Configuring TrueNAS CORE
Enter the IP address of the TrueNAS Core computer into the browser of another computer on the same network. We’re using an Ubuntu computer. The TrueNAS Core login window appears.

Enter “root” as the username and use the password you created earlier. Once you’re authenticated and logged in, you’ll see the TrueNAS CORE dashboard.
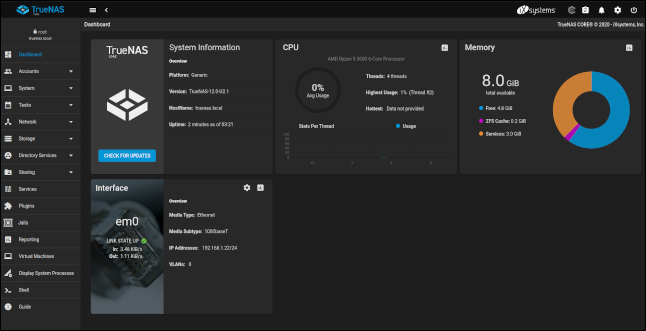
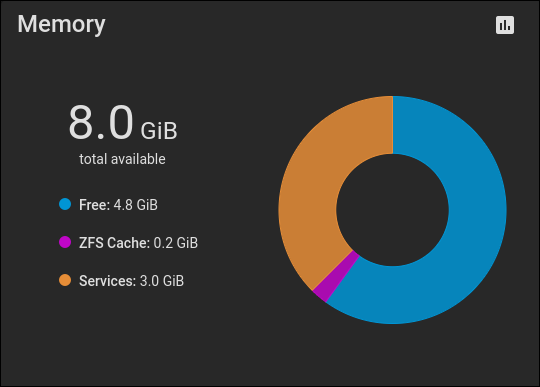
The main display contains panels of information. They show the real-time status of your TrueNAS CORE installation. For example, here is the memory panel:
There’s a side-panel at the left-hand edge of the display. It holds a list of options. You’ll use these options to configure your TrueNAS CORE. Here’s the top of that list of options.
Notice that the name of the currently logged-in user and the network name of the TrueNAS CORE computer are shown above the options.
Setting Up a Pool
A pool is a collection of hard drives that have been added to a single virtual device. The device is treated as if it were a single drive, and the ZFS file system handles the distribution of the data across the different physical drives.
In the options list select Storage > Pools. There are no pools in the system yet.
Click the blue “Add” button at the far right of the display. You can import an existing pool or create a new pool.
We need to create a pool, so accept the defaults and click the “Create Pool” button. The “Pool Manager” window appears. You need to name your pool. We used “pool1.”
The available hard drives are listed for you. The computer we’re using has two 500 GB hard drives in it for data storage.
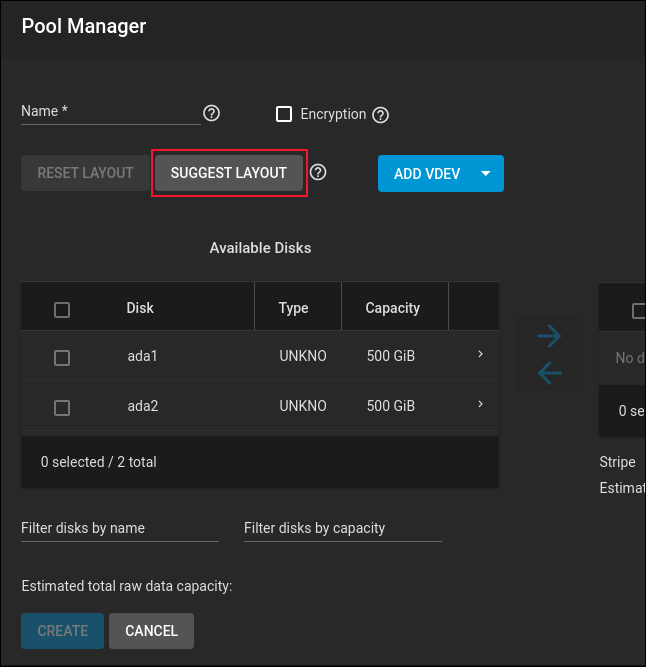
If you click the “Suggest Layout” button TrueNAS CORE will make a sensible choice of combination of drives, RAID, and mirroring.
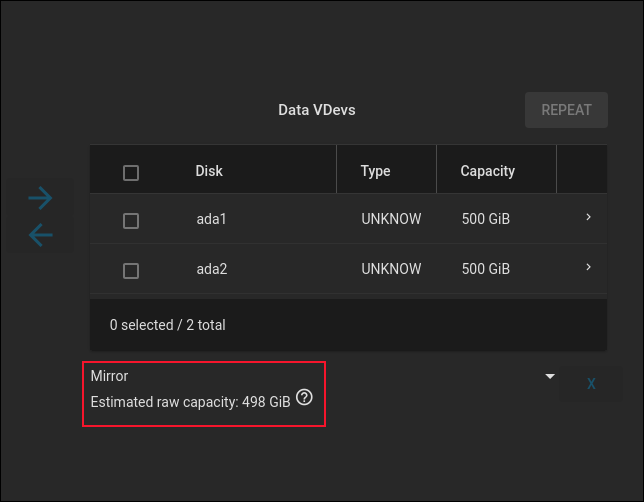
In our example, it used both drives in a virtual device and mirrored them. This gives 100% redundancy because both disks are a copy of each other. Our storage capacity is (almost) 500 GB, the same as one of the mirrored drives.
Click the blue “Create” button to create our new pool. A confirmation window appears.
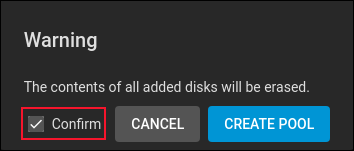
Click the “Confirm” checkbox and click the “Create Pool” button. The data drives are formatted to ZFS during this step. Our new pool, “pool1”, is listed in the pool list.
Creating Datasets
We’re now going to create a dataset in our pool. A dataset is a ZFS construction that behaves like a filesystem. Click the three-dotted menu button over to the far right of the “pool1” line.
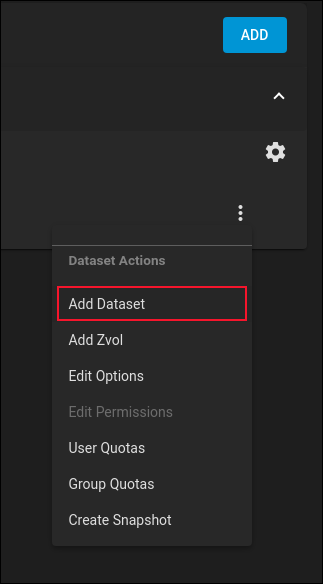
Select “Add Dataset” from the drop-down menu. The “Name and Options” dialog appears.
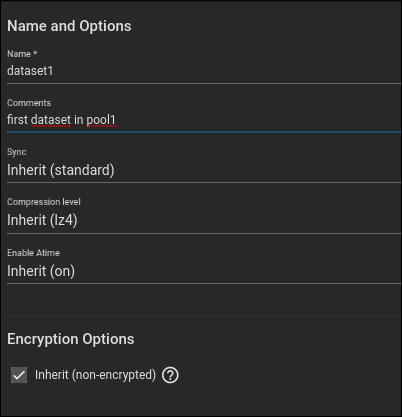
You need to name your dataset. We’ve used “dataset1.” Enter whatever you think will be useful to you in the comment field. You can accept all the other defaults and click the blue “Submit” button at the bottom of the dialog box.
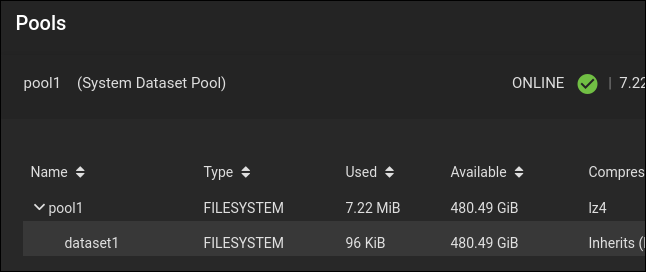
Our new dataset, “dataset1”, is listed as a child of our pool, “pool1.”
Now we’re going to create another dataset inside “dataset1.” This will be where a user called “dave” is going to store his data. Click the three-dotted menu button over to the far right of the “dataset1” line, then click “Add Dataset” in the drop-down menu.
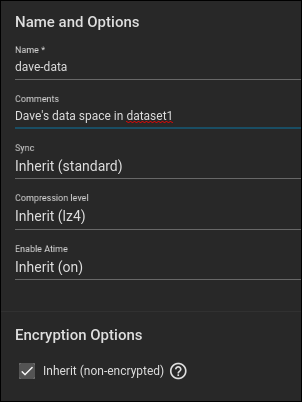
We called our new dataset “dave-data”, added a comment, and accepted all other defaults. Click the blue “Submit” button at the bottom of the dialog box.
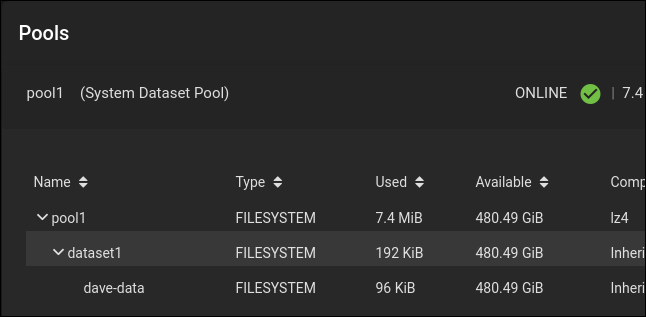
Our “dave-data” dataset is listed as a child of “dataset1.”
If you have several users who will use the TrueNAS Core, create more datasets—one per user—as children of “dataset1.” That way they can share the storage capacity of “dataset1” but only see their own files. We’ve only got a single user so we don’t need to create more datasets.
Creating Users
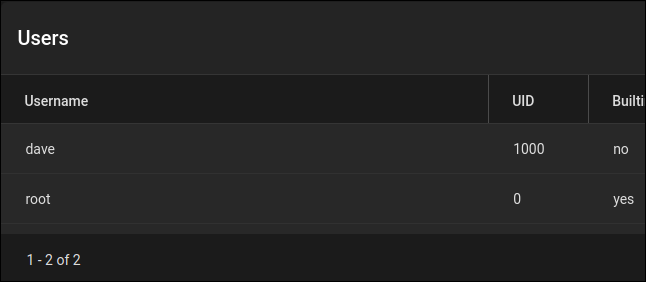
In the options list, click on Accounts > Users. The “Users” list appears. The only user listed is “root.”
Click the blue “Add” button at the far right of the display. The “Identification” dialog appears.
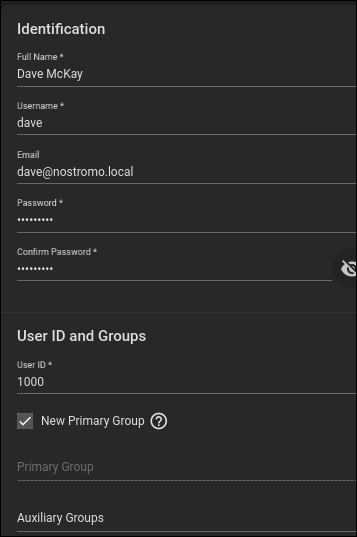
Complete the fields in the top half of the dialog box. You need to provide a full name and a user name. It’s convenient to use the same name as the user’s Linux account name. You can provide an email address if you like.
Provide a password, and enter it once more to verify you typed it correctly. Don’t use the same password as the user’s Linux account. Leave the “New Primary Group” checkbox selected, and scroll down to see the bottom of the “Identification” dialog.
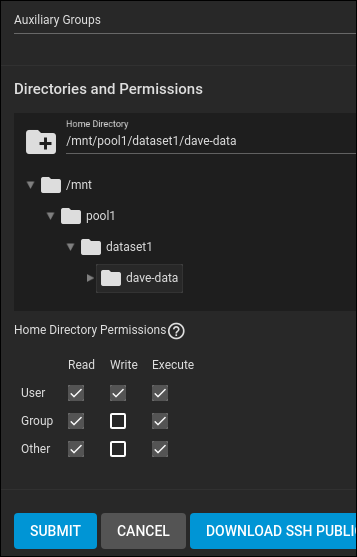
Expand the directory tree until you find the “dave-data” dataset. This is where the user’s “home” directory will be created. There is no “/home” directory in the operating system (which is FreeBSD) because TrueNAS CORE doesn’t want you to be storing files on the OS drive.
Click the blue “Submit” button to create the user.
Sharing the User’s Dataset
For a user to send files to TrueNAS CORE they have to be able to access their dataset remotely. We’re going to accomplish that in a couple of ways. The first is going to use a Network Filing System (NFS) share.
In the options list, click on Sharing > Unix Shares (NFS). The “Sharing / NFS” list appears. There are no shares listed in it yet.
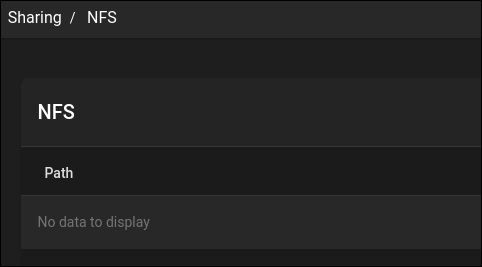
Click the blue “Add” button at the far right of the display. The “Paths” dialog appears.
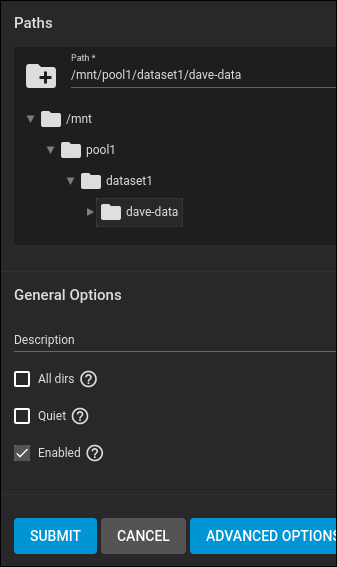
Expand the directory tree until you see the “dave-data” dataset. Click the blue “Submit” button to create the share. You’re asked whether TrueNAS CORE should start the NFS service.
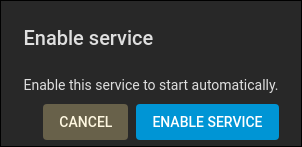
We’re definitely going to need that, so click the “Enable Service” button.
The new share is listed in the “Sharing / NFS” list.
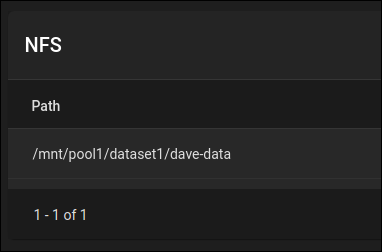
Configuring Services
We need to configure the services we’re going to use to access TrueNAS CORE. For this test, we’re going to connect to TrueNAS CORE in two different ways. One of those is via the NFS share we just configured and the other is via Secure Shell (SSH).
In the options list, click on “Services.” The list of services is displayed. Scroll through it until you see the “NFS” entry.

Because we told TrueNAS CORE to start the service for us, the slider is already set to “on” for us, and is colored blue. Click on the checkbox to have the service started automatically when TrueNAS CORE boots up.
Click on the pencil icon at the end of the NFS entry line to open the “General Options” dialog.
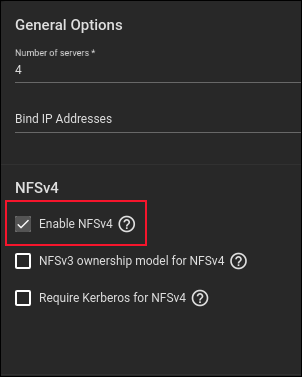
Click the “Enable NFSv4” checkbox, then click the blue “Save” button at the bottom of the dialog. Look through the services list and locate the SSH entry.
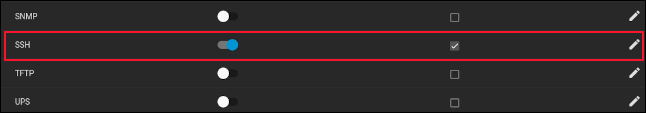
Click the slider so that it moves to the right and turns blue, and click the checkbox so that it has a tick in it.
Setting Permissions on Datasets
We’ve created a pool of drives, added a dataset, then added another dataset for the user “dave.” We’ve created the user “dave”, and we’ve enabled the services we’re going to use to connect to TrueNAS CORE.
The step that ties this all together is setting the permissions on the user’s dataset so that they are allowed to connect to it. In the options list, click on Storage > Pools, then click on the three-dotted menu at the end of the “dave-data” list entry.
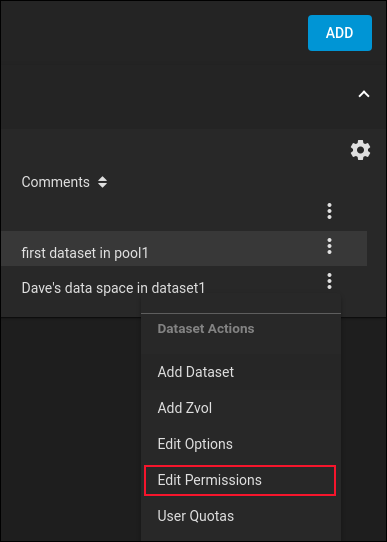
Click on the “Edit Permissions” menu entry.
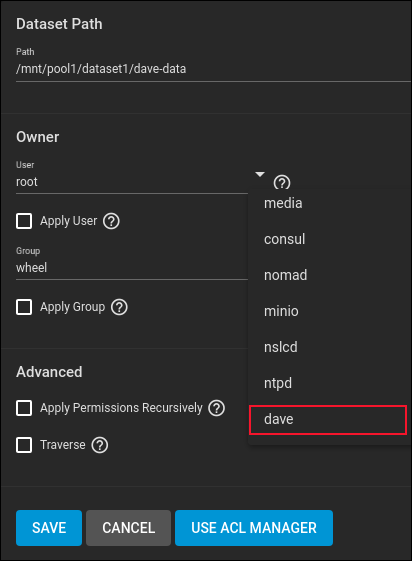
Use the drop-down menus to set the “user” and “group” fields to “dave.” Make sure you click on the “Apply User” and “Apply Group” checkboxes so that they are selected.
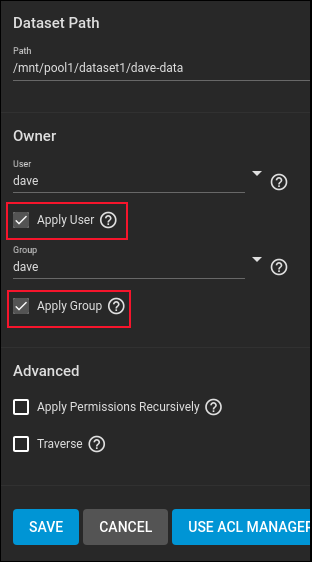
Click the blue “Save” button.
Connecting from Ubuntu
Connecting with SSH
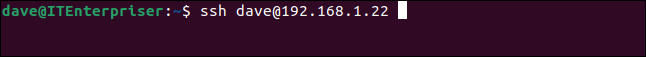
On the Ubuntu computer, open a terminal window and type the following command to connect to the TrueNAS CORE computer using SSH. Substitute the name of your user and the IP address of your TrueNAS CORE computer in the command:
ssh dave@192.168.1.22
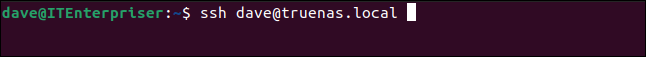
You can use the network name of the TrueNAS CORE if you prefer:
ssh dave@truenas.local
Once you’ve entered your password you’ll be connected to the TrueNAS CORE computer, in your user’s home directory. The command prompt will remind you you’re in a remote session on the TrueNAS CORE computer. The directory will be empty.
ls

To disconnect, use the exit command.
exit
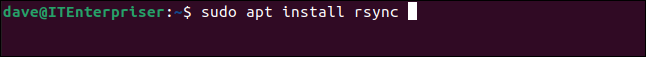
We’ve verified we can connect to the TrueNAS CORE computer via SSH. Let’s use SSH to send some data to the TrueNAS CORE. The rsync file syncing and backup utility uses SSH to transfer files. If you don’t have rsync installed on your computer you can install it with:
sudo apt install rsync
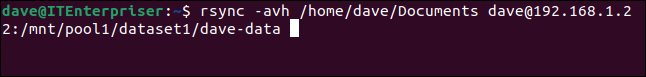
Here’s the rsync command we’re using.
rsync -avh /home/dave/Documents/ dave@192.168.1.22:/mnt/pool1/dataset1/dave-data
You’ll be prompted for the password of the “dave” account on the TrueNAS CORE—not your Ubuntu Linux account password—and then the file transfer takes place.
Connecting via NFS
Because we configured TrueNAS CORE to share the user’s dataset by NFS, we can mount the shared dataset on our Ubuntu computer and access it as though it were a local directory.
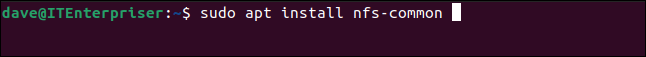
If you don’t already use them you’ll need to install the NFS utilities.
sudo apt install nfs-common
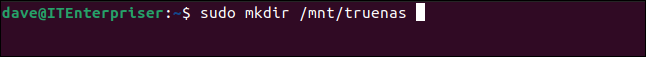
Now we’ll create a mount point to mount the remote dataset on.
sudo mkdir /mnt/truenas
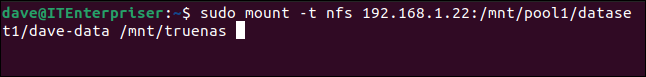
Now we’ll mount the remote dataset:
sudo mount -t nfs 192.168.1.22:/mnt/pool1/dataset1/dave-data /mnt/truenas
When you break that command down, it isn’t as bad as it looks.
- sudo: We need root permissions to execute the
mountcommand. - mount: The
mountcommand performs the mount action for us. - -t nfs: We need to tell
mountthat we’re mounting an NFS share. We do this using the-t(type) flag. - 192.168.1.22:/mnt/pool1dataset1/dave-data: The location of the NFS network share.
- /mnt/truenas: Where we want the share to be mounted.
of course, you’ll need to use the IP address and dataset name and path that you have set up on your system. Once the NFS share has been mounted you can browse to it just like any other location on your computer.
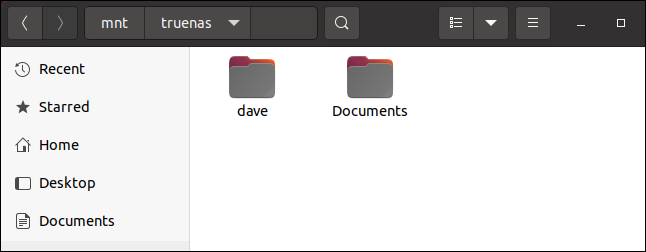
By browsing to the mount location on your Ubuntu computer you’ll see the remote dataset just as though it were a local directory. It contains the home folder of the user “dave” and the files in “Documents” that we copied across earlier using rsync.
If you press “Ctrl+D” in your file browser while you’re in the mounted NFS share, it is added to your file browser list of locations as a bookmark, which is convenient.
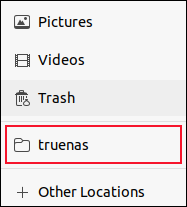
This proves we can mount the remote dataset, and that everything is working fine. But you don’t want to have to remember to mount the share each time you use your computer. So let’s automate that.
Automatically Mounting the Shared Dataset
To have the shared dataset mounted automatically at boot time, you need to add a command to the fstab file system table file.
sudo gedit /etc/fstab
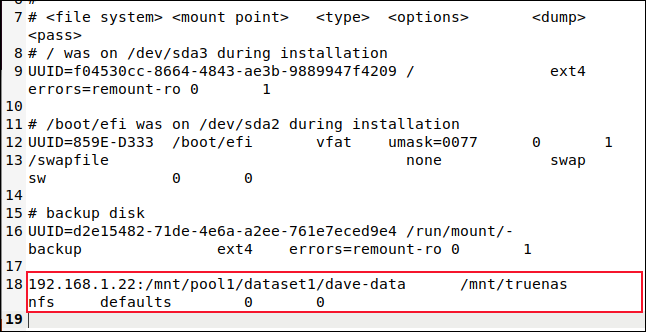
The line we need to add at the bottom of the fstab file looks like this. Make sure you use the IP address of your TrueNAS CORE, your shared dataset name, and the name of your mount point.
Also, take care to use the “Tab” key between the different parts of the command—don’t use spaces. Enter the whole command on one line, and hit “Enter” at the end to start a new line.
192.168.1.22:/mnt/pool1/dataset1/dave-data /mnt/truenas nfs defaults 0 0
Although the text has wrapped round in our screenshot, the command is actually all on one line:
Save the file and close the editor. Now, when you reboot your Ubuntu computer, your TrueNAS CORE dataset will be automatically mounted for you.
Next Steps
Congratulations, you’ve got a basic TrueNAS CORE system set up and working. We’ve only scratched the surface here. TrueNAS CORE is extremely richly-featured and there’s a lot more it can do.
Take the time to explore all the options in the sidebar option list to get an idea of what other features might be useful to you. Then—before you turn them all on—read the excellent documentation to see how to use them.
Also, consider creating an account on the TrueNAS Community forum, and benefit from the expertise of many other users.
The post How to Set Up TrueNAS CORE and Connect to it From Ubuntu appeared first on ITEnterpriser.
]]>The post What is Information Security? appeared first on ITEnterpriser.
]]>Same But Different?
Cyber security is the name for the suite of behaviors, controls, and technologies that make up an organization’s response to the risk of a cyberattack. Cyber security protects data, hardware, users, and the organization itself from all types of cyberthreats.
Related: 32 Cyber Security Terms Everyone Should Know
Information security—infosec—is concerned with protecting information. That includes unauthorized access or destruction, but it also includes the unlawful use of the information, and its unauthorized disclosure, disruption or modification. And notably, the information need not be stored digitally: information security also includes physical records.
So cyber security is about protecting all of your IT and cyber-based assets and activities, whereas information security is solely concerned with information. Infosec safeguards the information and ensure that it is gathered, processed, and transmitted lawfully.
Some of your infosec objectives will be satisfied by virtue of your general cyber security efforts, but other infosec objectives are governance measures or physical controls that you must implement, maintain, and run to satisfy the organization’s needs as well as any applicable data protection legislation.
Also, information is not the same as data. Not all data is information. Data is raw values. Only when the raw data is interpreted and infused with meaning does it become information. But we’re not going to go down this philosophical rabbit hole. The information we’re discussing is private knowledge about topics such as your organization, products, staff, or business relationships whether it is stored in a digital or physical medium.
The Objectives of Information Security
Personally identifiable information (PII) in particular must be adequately protected, and information such as medical information or information relating to children should be considered special category or sensitive information. Your local data protection legislation such as the General Data Protection Regulation or the California Consumer Privacy Act will list which categories of information are classed as special category data.
Your infosec activities should be designed to ensure the integrity, confidentiality, and availability of the information.
- Confidentiality: Controlling who has access to the information and how they may share or otherwise disclose the information will preserve the confidentiality of PII and other sensitive business information.
- Integrity: You must safeguard and protect the information so that unauthorized modification or destruction of the information is not possible. This preserves the quality and authenticity of the information.
- Availability: The information must be available to those who have authorization to access and use it. Unavailability can be a noncompliance under certain data protection legislations, such as GDPR.
These three principles gave rise to the well known three-letter acronym CIA. In addition to these, information security incorporates the principle of non-repudiation.
- Non-Repudiation: Repudiation is when someone denies receiving some information that was transmitted to them, or the sender denies sending the information, or there is a suspicion that the information was altered in transit. Cryptography can help here, if digital signatures and private keys are used. The data cannot be altered in transit because of the encryption. The digital signatures prove who sent the information. Message tracking and delivery verification can prove that the information was delivered.
- Authenticity: This requires that users are robustly identified and that it can be verified that the information received has genuinely come from a trusted sender. The digital signature is usually produced by creating a hash value of the sender’s private key and the message content. The recipient can decrypt the message with the sender’s public key which generates another hash value. If the message is hashed once more and the two new hashes match, the transmission can be considered authentic.
- Accountability: Accountability means having the ability to audit the actions of individuals and to trace the individual who performed an action. It also requires a change request procedure for changes that are not able to be made by the average user and are managed on their behalf by an authorized team or department.
Information Security Governance
Within your IT governance framework of policies and procedures, you will have an overall IT Security Policy. Depending on the size of your organization, the needs of your organization, and the demands of local legislation you may have appointed a Chief Information Security Officer (CISO) or a Data Protection Officer (DPO). These roles are not entirely equivalent. Briefly, a CISO is concerned with security and confidential data, and a DPO is focused on privacy and personal data.
A CISO and a DPO are not directly equivalent roles. A DPO can request—straight to the highest level of management—that, for example, penetration testing takes place or that another security measure be implemented. A CISO can generally make it happen.
If you don’t have a CISO then someone else must take responsibility for infosec. This isn’t something that can be tossed at IT just because it looks like a networking and security thing. Infosec isn’t IT, although IT is involved—just as infosec isn’t cyber security but cyber security is involved. When you allocate these roles beware of conflicts of interest. In fact, Article 38, Clause 6 of the GDPR forbids a DPO from having other tasks and duties that may result in a conflict of interests. So they can’t be your head of IT.
Whoever holds the post of CISO or DPO must have input to your governance framework to ensure that the particular needs of infosec are met, as well as satisfying relevant data protection legislation. Your governance has to have provisions to ensure the integrity, confidentiality, and availability of your information, and that you are street legal. That means the information must be collected, stored, processed, transmitted, and deleted in accordance with data protection legislation or any other standards that you have adopted, and that any rights the data subjects have regarding their data are upheld by your organization.
Your general security governance should call for the following measures:
- Technical: Technical measures include all hardware and software that protects data. Firewalls, encryption, intruder detection systems, and end-point protection suites are technical measures.
- Organizational: Organizational measures include the infosec governance framework, and the measures and resources, including human, that are deployed to uphold the requirements laid out in the policies and procedures.
- Human: This includes staff awareness training, education, and recruitment for suitably skilled candidates for key infosec positions.
- Physical: These measures include controlled and restricted access to digital information stores and asset clusters such as server rooms and data centers, and also to areas where physical records are stored.
In addition to the infosec-related entries in the general IT governance documentation you need to have a dedicated Information Security Policy. This should include such sections as:
- Purpose, Scope, and Objectives: A section describing the purpose of the infosec program, its scope within the organization—is it company-wide or site specific—and its overall objectives.
- Access Control: A description of the access controls that are in place, and what an employee must do to apply for access.
- Operations Plan: An operations plan is the set of active provisions that are designed to ensure that your information is always available to those who need it.
- Responsibilities: A list of the organization’s staff roles and positions that are involved in the safeguarding, including who is ultimately responsible for infosec. Nominated individuals
- Glossary: A glossary of key terms used in the document. Whoever reads it must understand it. Impenetrable policy documents are not impressive, they are an impediment to their own efficacy.
It’s About Handling Risk
Like cyber security, information security is about risk. Understanding the risks, using technology and other measures to mitigate the risks, and governing the use of information through policies and procedures to ensure that it is used safely and lawfully.
The post What is Information Security? appeared first on ITEnterpriser.
]]>