Whistleblowing is a catch-all term for disclosing wrongdoing in an organization. Not everyone will agree it’s for the greater good, so to be safe you need to be anonymous. Here’s how.
Types of Whistleblowing
Whistleblowing is the common name for what is more formally called making a disclosure. It can mean bringing some wrongdoing to the attention of management within an organization, or to external authorities, or to the attention of the public via the media. in extreme cases, it can involve disclosing to the outside world of wrongdoings by a government or other ruling faction in an oppressive regime.
Not everything you may disclose will count as whistleblowing. Reporting these types of event are considered whistleblowing:
- A criminal offence, for example someone is defrauding your organization. The organization is the victim.
- An organization is breaking the law. The organization is the wrongdoer.
- Something that jeopardizes the health or safety of a person.
- Something that either puts the environment at risk or actually damages it.
- A miscarriage of justice.
- Someone is covering up a wrongdoing.
- Violations of human rights.
However, anything to do with bullying, harassment, or discrimination at work is not considered whistleblowing in most jurisdictions. The difference is important.
Whistleblowers are protected by law in many countries. In the U.S. the Whistleblower Protection Act of 1989 protects federal whistleblowers. In the United Kingdom, the Public Interest Disclosure Act 1998 provides similar protection and the “right not to suffer detriment” for whistleblowing. In Europe, the EU Whistleblower Directive protects people who report breaches of European Union law.
There are many other pieces of legislation and statutes that uphold the rights and protection of whistleblowers. The U.S. Department of Labor’s Occupational Safety and Health Administration has a Whistleblower Protection Program. It protects workers from detriment should they report a breach in any of more than 20 federal laws.
Who Do You Disclose to?
What you’re disclosing will usually dictate who you disclose it to. If it is something about a colleague you’ll probably be reporting it to a member of the management team of your organization. Many organizations have a whistleblowing process. This should outline the steps they have in place to safeguard your anonymity.
If you’re unhappy about revealing your identity because of fear of reprisals, you can report the wrongdoing anonymously. There can be an awkward balance at play here. Your organization may or may not be able to proceed with the complaint if you withhold your name, but providing your name gives rise to a risk of exposure. If you’re whistleblowing on your manager it would create an untenable situation if they later discovered who the whistleblower was.
There might be a prescribed person or body that you can disclose to anonymously. If you’re reporting an organization and not an individual, it will usually be to a prescribed body, professional body, or a trade association.
If you’re wanting to draw world attention to a breach of human rights you’ll need to approach an organization like the United Nations.
You can also whistleblow to the media to bring wrongdoings to the attention of the public and the relevant authorities. Most major media organizations have guidelines regarding anonymous sources. Online resources like WikiLeaks are also popular with whistleblowers.
The media organization will probably require your name in order to pursue the story, but you’ll be protected as an anonymous source. This is a right accorded to journalists by law in many countries and under international law. It prohibits attempts to compel them to reveal their anonymous source. This is doubly important because whistleblowing to the media waives your rights in law to protection as a whistleblower. Without anonymity—or if your anonymity is broken—you will face the possibility of reprisals.
- You might get demoted, repositioned, transferred, or lose your job altogether if you are still working at the organization in question when your identity is revealed.
- You might be seen as untrustworthy and a traitor. You might become the victim of workplace bullying.
- Other businesses in the same industry could add you to a blacklist, making future employment difficult if you choose to leave your current organization.
- You might face legal action if you break any laws to gather evidence to justify or support your whistleblowing claims. Even with the legal protection for whistleblowers, there is no protection for breaking the law.
- If you’re whistleblowing on an oppressive regime your life may be at risk.
Preserving Your Anonymity
Communicating and delivering documents anonymously isn’t as easy as you might think. Almost everything we do to communicate or transmit data leaves a trail of breadcrumbs that can lead right back to you or has a log that records what you did and when. It isn’t easy to act anonymously, but it isn’t impossible either. Knowing what type of tracking and logging exists allows you to avoid many common mistakes.
The run-of-the-mill email account isn’t anonymous. It is tied to your identity so that you can receive your email. And you have to provide information about yourself—and verify it—before you can set up most email accounts. And anyone who can access the email system logs—either through administrative capabilities or via a subpoena—can see who you have been communicating with.
However, there are free, secure, privacy-focused, and anonymous email services that you can use. ProtonMail is one of the better known. Your email is encrypted. Even ProtonMail cannot access your emails. It’s a web-based service so you don’t need to have an application installed anywhere to send or read your email.
Crucially, you can sign up for the ProtonMail service without providing any information about yourself. They do ask for some means to contact you in case you lock yourself out of your account and they need to verify it is you before they restore access to you. However, that is optional. If you don’t want to, you don’t need to provide any information about yourself at all. Just make sure you don’t forget your password.
You’ve now got an email address that is secure, encrypted, and not linked to your identity in any way. But now you have to be able to use it so that your online activity doesn’t point back to you.
Exfiltrating Data: Gathering the Evidence
There’s a great saying “computers serve their owners, not their users” and it’s good to keep that in mind. If you’re using someone else’s computer you don’t know what is being logged. It could be anything from the usual internet browser activity and system logs to a full corporate employee monitoring system. These systems can:
- Capture keystrokes.
- Detect file copy actions.
- Detect document creation, edits, and deletions.
- Detect and log, or prevent, the use of a USB memory drive.
- Take a screenshot every few seconds.
But even in the absence of employee monitoring software, you can’t trust a corporate computer, an internet cafe computer, or the computers in your library. You can’t purge and clean them to remove all traces of your activity. Router and firewall logs also track what you do. And you might well be on CCTV too.
Obviously, don’t use your work computer for whistleblowing activities, and don’t check your ProtonMail from your work desk. But the problem is, if you need to exfiltrate files that contain evidence of the wrongdoing how can you achieve that?
If you have a hard copy of the files and it is feasible, you can photocopy them. If that’s out of the question—some corporate photocopiers require an ID to identify the employee before they can be used—covertly remove the hard copies that you have. You can then scan them or photograph them at home and return the originals when you’ve finished. Don’t take them to a photocopy shop.
Trying to covertly print at work is dangerous. Large corporate printers log who has printed what and when. Some of them even keep copies of the documents that pass through them. And printing at home isn’t anonymous either if you have a color laser printer.
Many domestic color printers fingerprint pages with tiny yellow on white dots that identify the time, date, and serial number of the printer the printouts came from. If you’re considering sending a letter or a covering note with the exfiltrated documents, don’t use a color printer.
If hard copies are not a possibility and you have to gather electronic documents, you have some options. The hard part is knowing which of the possible actions is going to be detected and reported as a suspicious activity—if any. Some organizations are lax when it comes to data protection automation.
You may be able to upload files to private cloud storage such as OneDrive, Google Drive, DropBox Evernote, or an anonymous, free, file-sharing site like GoFile.
If you have administrative access to a private website you can try using a File Transfer Protocol (FTP) browser plug-in and FTP the files to the storage in the website.
Plugging a smartphone into a computer’s USB port to charge it is common practice. But smartphones can also store files, allowing data to be copied to them as though they were a USB memory drive. If USB drive access hasn’t been turned off, this might be less eye-catching than using a regular USB drive.
Emailing files is too traceable to be anything other than a dire, last-ditch option.
If you’re not going to be caught on CCTV camera, taking photographs of your screen or of the hardcopy documents is a long-winded possibility.
Dealing With Metadata
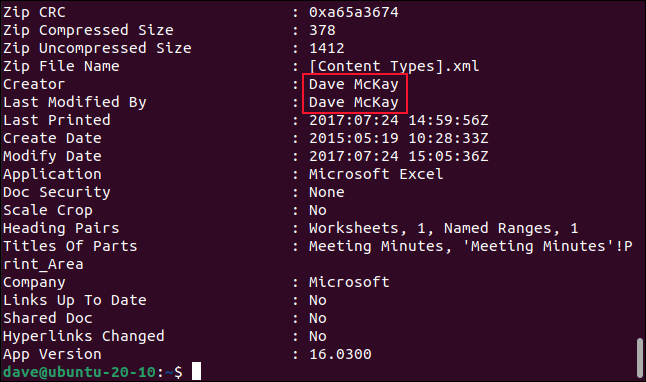
Electronic documents, especially those created with office productivity suites such as Microsoft Office contain metadata. Metadata is data that describes the document itself. It is automatically created by software applications. Metadata holds information such as:
- The name and version of the package that created the document.
- The name (or network ID) of the original author.
- The date and time when the document was created.
- The name (or network ID) of the person who last edited the documents.
- The date and time when it was last edited.
Some of that data could incriminate you.
Photographs taken with a digital camera or a smartphone contain a wealth of information about the image including when it was taken, the details of the device used to take the photograph, and the GPS coordinates of where the image was taken. If you’ve taken hardcopy documents home and photographed them the GPS location of your home is likely to encoded within the images. That will directly implicate you as the whistleblower.
Here are the number of pieces of data found in a few sample files from one of my computers. Your documents may contain even more metadata than these, depending on your device and software settings.
- 45 Metadata Fields: Microsft Word “.docx” word processing file.
- 34 Metadata Fields: Microsft Excel “.xlsx” spreadsheet file.
- 102 Metadata Fields: JPG image taken on a smartphone.
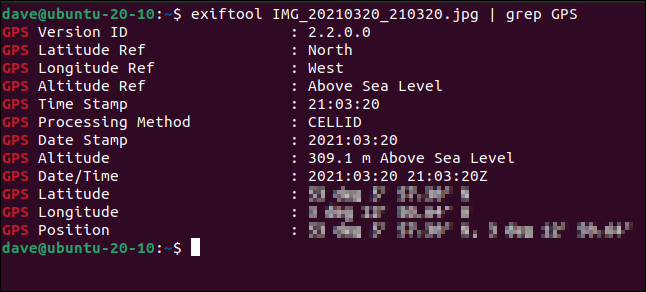
Clearly, if you are going to deliver electronic documents and images to your contact and you wish to remain anonymous you need to erase or edit the metadata. Free tools exist for this and are available for all common computing platforms. ExifTool is one of the most capable. It is free, cross-platform, and capable of working with the metadata of over 190 different file types.
ExifTool is a command-line tool, but if you’re not comfortable with the command line you can download jExifToolGUI, which is a free, cross-platform GUI for ExifTool that works on Windows, Mac, and Linux.
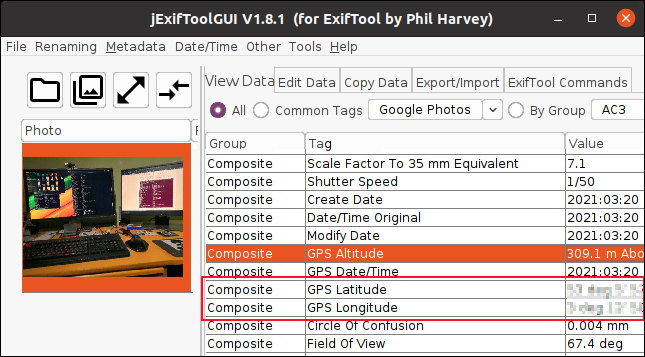
jExifToolGUI makes it easy to delete metadata fields that contain information that could be a clue to your identity.
Making the Disclosure
Assuming you have gathered the evidence, you need to make the disclosure. That means making contact with the party you are disclosing to. Most major newspapers and many other organizations have a means of obtaining anonymous news stories and tip-offs, using SecureDrop to provide a portal for file transfer. Because SecureDrop portals are hosted on the Dark Web you’ll need to use a Tor-enabled browser such as the Tor browser to access them.
For example, the New York Times SecureDrop portal is located at: https://nytimes.securedrop.tor.onion, and can only be accessed using a Tor-enabled browser.
The Tor anonymous network makes it virtually impossible to backtrack and find out your IP address, so you cannot be identified. If you need to communicate with an organization that doesn’t use SecureDrop you should check their website for details of how to contact them for confidential matters. Use a Virtual Private Network at the least, and a Tor-enabled browser by preference, when contacting any site for any aspect of your whistleblowing. That includes the relatively benign act of finding out what the address of their SecureDrop portal is, or looking up other contact details.
Once you’ve made contact, leave your ProtonMail or other secure email address so that they can get back to you. Once you’ve communicated back and forth for a period of time and you’re comfortable with your contact, you may choose to connect with them using Signal Messenger, a secure, private messaging service.
Signal is private, but it isn’t anonymous. If the authorities want to, they can subpoena Open Whisper Systems—the creators of Signal—and find out whether you use the service, when you joined, and when you last used it. But that’s all they can discover because that’s all that the Signal services stores about you. No one can determine with whom you have communicated, or about what. If you want to have voice calls with your contact do it from your home, and use Signal’s voice call capability.
If you want to have the strongest possible protection for your online anonymity, use Tails. Tails is an operating system that sits on a USB memory stick or CD. You boot your computer using the image on the memory stick or CD, and it runs a privacy-focused minimalist Linux based on Debian. It already has the Tor browser installed for you.
You can check your secure mail, access secure portals, and do whatever you need to. When you shut down, remove the memory stick or CD and you can boot your computer back up as normal, into its usual operating system. Nothing on your computer will have any traces of what you’ve done. And Tails is an amnesiac operating system. It doesn’t track anything you do.
If you want to go a step further use public Wi-Fi, and Tails. But remember that many places have CCTV, including public transport, and that you should leave your smartphone at home because of its geolocational tracking. That can be used to place you at a location at a particular time which could be cross-referenced with the Wi-Fi router logs looking for encrypted or Tor connections. That could be enough to incriminate you.
If you’re going to post hardcopy files to your contact, use a post office that is outside your normal area and pay by cash. You need to avoid tying a payment card to a record of postage. Make sure there is nothing incriminating on the outside of the envelope or packaging. Every single item that is handled by the U.S. postal service is photographed. You should assume other countries have similar programs.
It’s Difficult, But Possible
Take all the defensive steps you can. Don’t just turn on incognito mode and hope for the best.










