A Brief History of the Floppy Disk
Ah, the floppy disk. How I miss thee. How I don't. There was a certain tactile pleasure to inserting you into your drive, and in the early days, locking you in place. The audible...
What is Cyber Security? Definition, Threats, and Defenses
As threats in the cyber world continue to grow, so does our need to protect ourselves from these threats. When discussing ways to virtually protect ourselves from these threats, the term cyber security often...
Securing Kuburnetes with StackRox
StackRox integrates with Kubernetes to secure clusters of containers by scanning container images during the creation, deployment, and runtime phases. Real-time alerting, dashboards, and standards compliance complete the picture.
The Outlook is Cloudy
There’s no stopping...
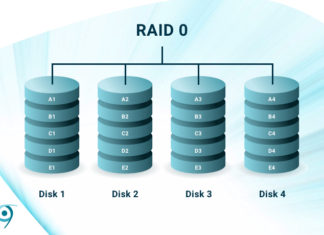
What is RAID 0? All Speed, No Safety
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single physical storage device. Depending on the type, or "level", RAID increases performance, capacity, and fault tolerance in some...
Artificial Intelligence: The Hackers’ New Weapon
Malware is getting smarter---literally. Threat actors are using artificial intelligence to create cyberthreats capable of learning and acting as autonomous agents that can change their tactics as required to complete their mission.
What is Artificial...
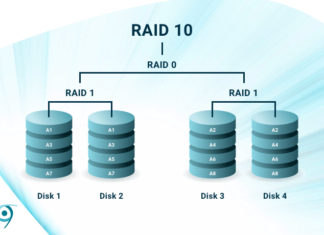
What is RAID 10? Speed and Fault Tolerance
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single physical storage device. Depending on the type, or "level", RAID increases performance, capacity, or fault tolerance, or some...
What is Btrfs? The Better (than most) File System
Btrfs may be a "better" file system next to everything except ZFS, but what Btr actually stands for is not "better", or "butter", but B-Tree, a data construct employed in the design. Now that...
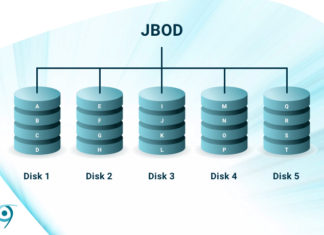
What is JBOD? Quick and Dirty Maximum Capacity
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single logical storage unit, i.e., a single drive. Depending on the type, or "level", RAID increases performance, capacity, and...
What is a VPN? Security and Privacy, Up To a Point
Virtual Private Networks (VPN) have been around for roughly thirty years. They provide secure communication between two networks, even over the public internet. What is a VPN? It’s how you communicate in public but...
What is a Spear Phishing Attack?
Spear phishing is sending illicit emails to someone to make them do something to the threat actor's benefit. What is a spear phishing attack? It's a one-on-one scam, and you're the target.
Phishing Versus...