A Brief History of the Floppy Disk
Ah, the floppy disk. How I miss thee. How I don't. There was a certain tactile pleasure to inserting you into your drive, and in the early days, locking you in place. The audible...
Top 3 Microsoft Office 365 Backup Solutions
Mention data safety, and backup will instantly spring to mind. What is not immediately available, even to seasoned IT professionals, is information about what makes a good backup solution. With more businesses embracing Microsoft...
FreeNAS vs. UnRAID: What are the Differences?
To the outside world, FreeNAS (TrueNAS) and UnRAID appear far more alike than different. In effect, they are. Both are operating systems that allow you to leverage your own hardware as a NAS (Network...
What is a VPN? Security and Privacy, Up To a Point
Virtual Private Networks (VPN) have been around for roughly thirty years. They provide secure communication between two networks, even over the public internet. What is a VPN? It’s how you communicate in public but...
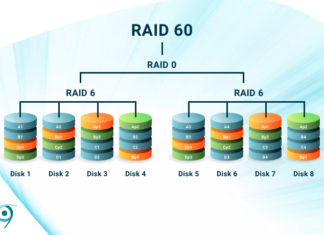
What is RAID 60? Double-parity and More Speed
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single hardware storage device. Depending on the type, or "level", RAID increases performance, capacity, and fault tolerance in some...
What is UnRAID? Outstanding Capacity with Parity
There are a number of NAS operating systems out there, including several based on the BSD (Berkeley System Development) operating system. Most are proprietary to the vendor, but several are not. The most unique...
What is ZFS? The File System other File Systems Aspire to
File systems are what make organized data storage possible, and quite a few have appeared over the years: FAT32, exFAT, NTFS, Ext2/3/4, Btrfs, HFS, APFS, etc. However, there's one file system that outshines them...
What RF Attacks Are and How to Defend Against Them
Firewall and rules are in place, intrusion detection systems are running, and all industry best practices are being followed. Great, but what about Radio Frequency attacks? They nimbly sidestep all of that.
Radio Frequency Attacks
Firewalls...
Shielding Your Computer From Malware During the COVID-19 Pandemic
Hackers are the bad eggs in the cyber world that try to make use of any opportunity to steal information or money. Characteristically, they latch onto vulnerabilities and security loopholes to exploit computer users....
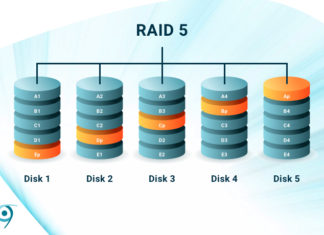
What is RAID 5? Good Speed, Safety through Parity
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single physical storage device. Depending on the type, or "level", RAID can increase performance, capacity, fault tolerance, or combinations...