What is Btrfs? The Better (than most) File System
Btrfs may be a "better" file system next to everything except ZFS, but what Btr actually stands for is not "better", or "butter", but B-Tree, a data construct employed in the design. Now that...
A Brief History of the Floppy Disk
Ah, the floppy disk. How I miss thee. How I don't. There was a certain tactile pleasure to inserting you into your drive, and in the early days, locking you in place. The audible...
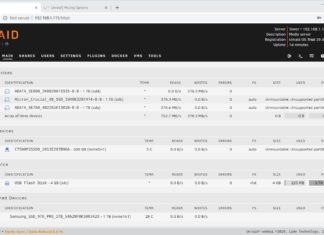
What is UnRAID? Outstanding Capacity with Parity
There are a number of NAS operating systems out there, including several based on the BSD (Berkeley System Development) operating system. Most are proprietary to the vendor, but several are not. The most unique...
What is a VPN? Security and Privacy, Up To a Point
Virtual Private Networks (VPN) have been around for roughly thirty years. They provide secure communication between two networks, even over the public internet. What is a VPN? It’s how you communicate in public but...
What is a Trojan Virus? A Master of Disguise
What is a Trojan virus? An impostor, a saboteur, and a master of disguise. But it isn’t actually a virus. Find out how this masquerading malware operates, and keep your systems safe.
What is...
What is iSCSI and What Do You Do With It?
I SCSI'd, you SCSI'd, we all SCSI'd (pronounced Scuzzy). In the days of ribbon cables, SCSI (Small Computer Systems Interface) was the end-all of storage and peripheral interfaces. Everyone computing at the time had...
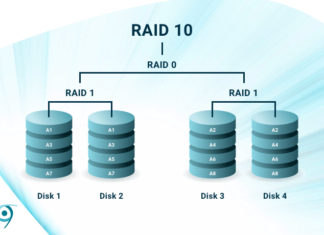
What is RAID 10? Speed and Fault Tolerance
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single physical storage device. Depending on the type, or "level", RAID increases performance, capacity, or fault tolerance, or some...
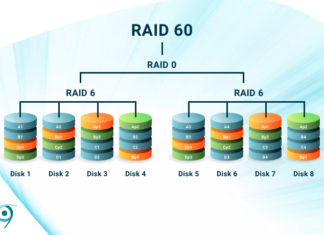
What is RAID 60? Double-parity and More Speed
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single hardware storage device. Depending on the type, or "level", RAID increases performance, capacity, and fault tolerance in some...
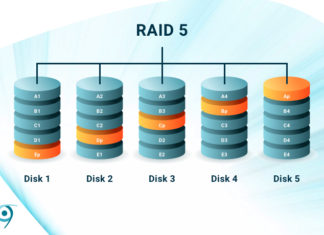
What is RAID 5? Good Speed, Safety through Parity
RAID (Redundant Array of Inexpensive Disks) is the combining of multiple disks to mimic a single physical storage device. Depending on the type, or "level", RAID can increase performance, capacity, fault tolerance, or combinations...
What is Cyber Security? Definition, Threats, and Defenses
As threats in the cyber world continue to grow, so does our need to protect ourselves from these threats. When discussing ways to virtually protect ourselves from these threats, the term cyber security often...